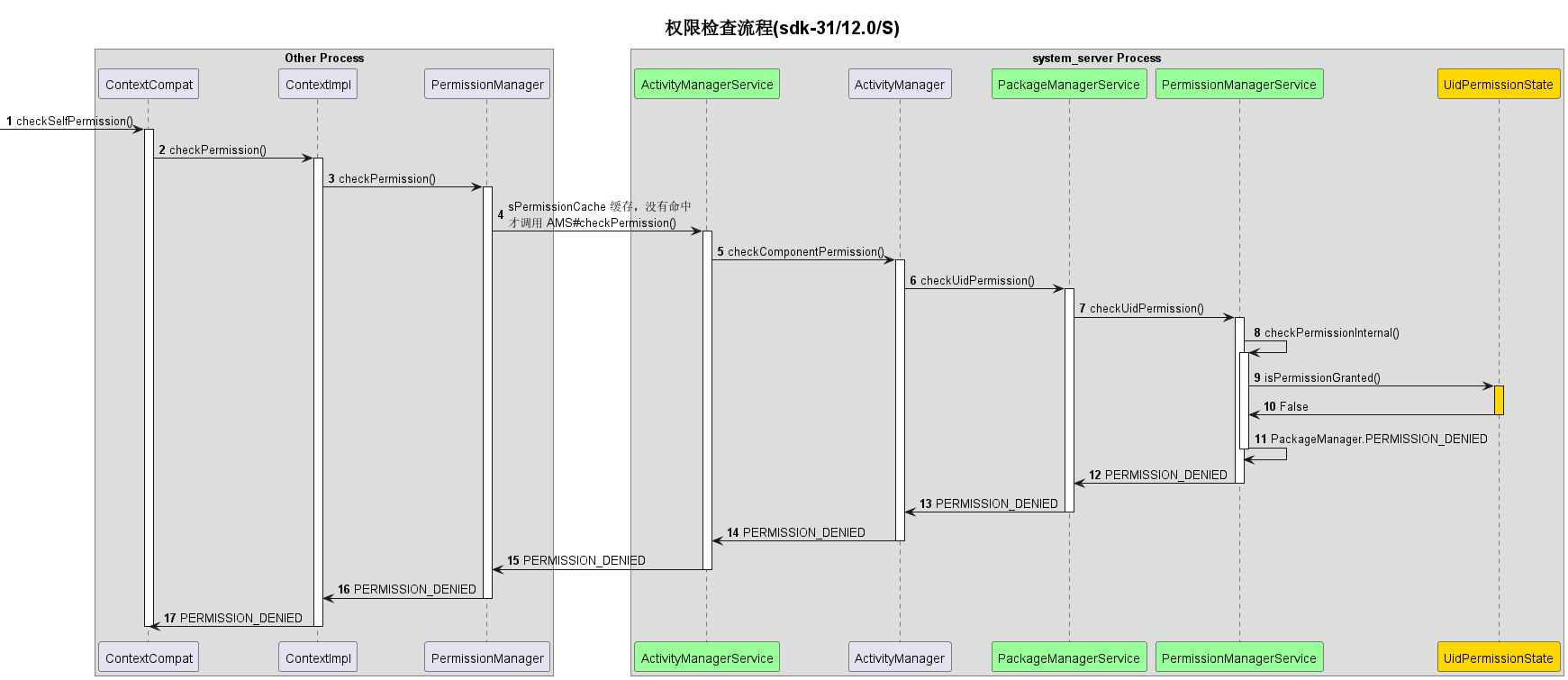
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
| public class PermissionManagerService extends IPermissionManager.Stub {
private class PermissionManagerServiceInternalImpl implements PermissionManagerServiceInternal {
@Override
public int checkUidPermission(int uid, @NonNull String permissionName) {
return PermissionManagerService.this.checkUidPermission(uid, permissionName);
}
}
private int checkUidPermission(int uid, String permName) {
if (permName == null) {
return PackageManager.PERMISSION_DENIED;
}
final int userId = UserHandle.getUserId(uid);
if (!mUserManagerInt.exists(userId)) {
return PackageManager.PERMISSION_DENIED;
}
final CheckPermissionDelegate checkPermissionDelegate;
synchronized (mLock) {
checkPermissionDelegate = mCheckPermissionDelegate;
}
if (checkPermissionDelegate == null) {
return checkUidPermissionImpl(uid, permName);
}
return checkPermissionDelegate.checkUidPermission(uid, permName,
this::checkUidPermissionImpl);
}
private int checkUidPermissionInternal(@Nullable AndroidPackage pkg, int uid,
@NonNull String permissionName) {
if (pkg != null) {
final int userId = UserHandle.getUserId(uid);
return checkPermissionInternal(pkg, false, permissionName, userId);
}
return PackageManager.PERMISSION_DENIED;
}
private int checkPermissionInternal(@NonNull AndroidPackage pkg, boolean isPackageExplicit,
@NonNull String permissionName, @UserIdInt int userId) {
final int callingUid = getCallingUid();
if (isPackageExplicit || pkg.getSharedUserId() == null) {
if (mPackageManagerInt.filterAppAccess(pkg, callingUid, userId)) {
return PackageManager.PERMISSION_DENIED;
}
} else {
if (mPackageManagerInt.getInstantAppPackageName(callingUid) != null) {
return PackageManager.PERMISSION_DENIED;
}
}
final int uid = UserHandle.getUid(userId, pkg.getUid());
final boolean isInstantApp = mPackageManagerInt.getInstantAppPackageName(uid) != null;
synchronized (mLock) {
final UidPermissionState uidState = getUidStateLocked(pkg, userId);
if (uidState == null) {
Slog.e(TAG, "Missing permissions state for " + pkg.getPackageName() + " and user "
+ userId);
return PackageManager.PERMISSION_DENIED;
}
if (checkSinglePermissionInternalLocked(uidState, permissionName, isInstantApp)) {
return PackageManager.PERMISSION_GRANTED;
}
final String fullerPermissionName = FULLER_PERMISSION_MAP.get(permissionName);
if (fullerPermissionName != null && checkSinglePermissionInternalLocked(uidState,
fullerPermissionName, isInstantApp)) {
return PackageManager.PERMISSION_GRANTED;
}
}
return PackageManager.PERMISSION_DENIED;
}
private boolean checkSinglePermissionInternalLocked(@NonNull UidPermissionState uidState,
@NonNull String permissionName, boolean isInstantApp) {
if (!uidState.isPermissionGranted(permissionName)) {
return false;
}
if (isInstantApp) {
final Permission permission = mRegistry.getPermission(permissionName);
return permission != null && permission.isInstant();
}
return true;
}
}
|